Odin ransomware: decrypt and remove .odin file virus
Learn what to do if you are infected with the Odin ransomware and how to restore files with .odin extension that this virus spawns all over the infected PC.
Ransomware that employs cryptography is probably the worst type of computer malware invented to date. The impact is highly disruptive because these infections take one’s personal files hostage by encoding them and threaten to never make the data accessible again unless a ransom is sent to the attackers. The Trojan called Locky, which was originally discovered in early 2016, precisely demonstrates the totality of these adverse effects. A few days ago, its code underwent a tweak as a new variant was rolled out. As opposed to the formerly used .zepto extension, the virus now appends the .odin fragment at the end of every encrypted file. Whereas the text of ransom notes hasn’t been changed, the names of these instructions are different than the previous edition would create on the desktop and affected folders. The recovery steps are now available in three versions, namely _HOWDO_text.html, _HOWDO_text.bmp, and an additional copy _[random 2 digits]_HOWDO_text.html dropped only into encrypted directories.
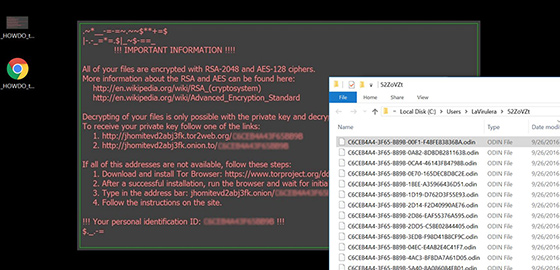
The Odin virus also makes filenames unidentifiable. Having enciphered the data, it replaces the original values with long strings consisting of 5 distinct blocks of hexadecimal characters. Consequently, a victim will be unable to find and focus on decrypting a specific file that may be the most important. All that’s left is myriads of weird-looking entries with the .odin extension, which the operating system does not recognize as valid. The ransomware under consideration applies two different cryptographic standards to arrive at the inaccessibility goal. First, it encodes files with AES-128 cipher and then secures the decryption key using another algorithm called RSA-2048. The private RSA key is sent to a C2 server so that no one but the criminals has access to it.
This malady propagates over spam. The targeted users receive fishy emails with a Windows Script File or JavaScript object attached to them. Once opened, the booby-trapped attachment instantly executes a DLL installer. To this end, it harnesses the rundll32.exe command so that antimalware programs don’t flag this instance as suspicious or clearly harmful. Next, the Odin ransomware starts traversing the hard drive and network shares in search of hundreds of different file types. Every item found along the way is going to be encrypted according to a pattern described above. To explain to the victim what happened and how to go about the predicament, the pest creates _HOWDO_text ransom directions in the most conspicuous places. These documents tell the infected person to open a certain web page via Tor Browser and follow the steps listed on the Locky Decryptor Page. The user needs to register a Bitcoin wallet, purchase 0.5 BTC (about 300 USD), and submit the coins over to the threat actors. Although the perpetrators promise to provide a decryptor afterward, there can be no confidence in this regard. If hit by the .odin file extension virus, try the methods below instead.
Odin ransomware removal
It’s usually quite easy to get rid of the offending program proper. Ransom Trojans are easy targets for antimalware suites once the data encryption part has been performed. This fact alone does not set aside the necessity of removing the infection, because it may cause further damage along with the likely escorting modules such as password stealers.
1. Download, install and run Odin removal software. Click the Start New Scan button and wait until the suite does a thorough system checkup.
Download .odin file virus remover2. When the scan results are readily available, go to Fix Threats and let the program do its cleaning job.
Workarounds to recover .odin encrypted files
Unless security researchers or AV labs release a dependable decrypt tool, recovering the scrambled files is somewhat of a lottery. However, there are techniques that ransomware victims shouldn’t fail to try before considering the buyout suggested by the criminals. Be sure to peruse and implement the methods below.
1. Backups
First and foremost, download backup copies of your important data from an offsite storage unaffected by the ransomware. In case you hadn’t had a backup strategy before the breach occurred,
proceed to the next step. Also, start maintaining secure backups of the most valuable information so that attacks like this one won’t cause that much damage in the future.
2. Shadow Copies
Odin is coded to obliterate Shadow Copies of its victim’s files, which are data snapshots automatically made by the operating system. The ransomware has reportedly failed to complete
this task in some cases, though. An important prerequisite of successful recovery is the ‘enabled’ status of the System Restore feature prior to the compromise. There are two ways
to take advantage of this functionality built into Windows.
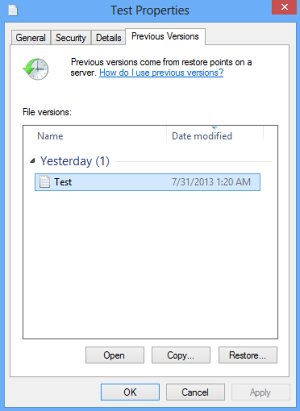
- Previous Versions Based on Restore Points
Select a random encrypted file, right-click on it and go to Properties. Now proceed to the Previous Versions tab. If the OS had been making snapshots of this file during system restore events, it will display the list of available file versions. Highlight the latest one and select Copy to recover it to a new path on the computer. Clicking the Restore button will reinstate the file to its original location.
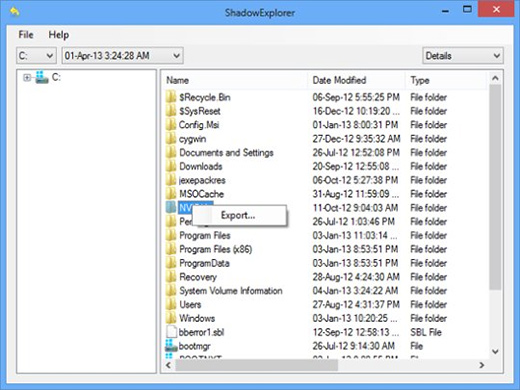
- ShadowExplorer
The applet called ShadowExplorer is meant to automate data recovery based on VSS (Volume Snapshot Service). If that’s the workflow of your choice, download and install the tool. Run it, select the local drive name and the folder of interest, right-click on it, hit the Export option and follow further prompts to get the job done.
3. Forensic Tools
The algorithm of data scrambling employed by most ransomware involves the deletion of original files, while their encrypted copies are the objects of the ransom bargain. Now, erasing
information off the hard drive is only irreversible when done with multiple overwrites. Otherwise, it may be possible to restore files using utilities like
Data Recovery Pro. Simply run the app and see whether it can do the trick.
Look before you leap into secure computing
Now that you have hopefully recovered your files, make sure the Odin ransomware will make no more trouble. Consider scanning the system for executables and leftover registry keys added by the infection. Double-checking is also a good idea because some of the newer variants of crypto malware are accompanied by other threats such as rootkits and identity theft programs. So run the scan again and see whether or not you are completely safe.