Cerber crypto virus: How to decrypt .cerber extension files
Ransomware called Cerber is absolutely one of a kind, because it employs a text-to-speech feature and uses cryptosystems immaculately.
There is a myriad of file-encrypting viruses on the cyber threat landscape, but the one dubbed Cerber stands out from the crowd. It was the first to introduce an audio warning mechanism, where victims can both read the ransom demands and literally listen to them. Such an effect is attained via a variant of decrypt instructions in VBScript format. The object titled # DECRYPT MY FILES #.vbs makes the compromised computer play back an alert when the user opens it, thus making the breach scarier. The aftermath of this attack is all about rendering one’s valuable data inaccessible due to the use of the RSA cipher to encode secret keys generated in the course of the AES encryption. The tandem of two strong cryptosystems is impossible to bypass unless you are the person that owns the private key. The files processed in this fashion get the .cerber tail concatenated to them.
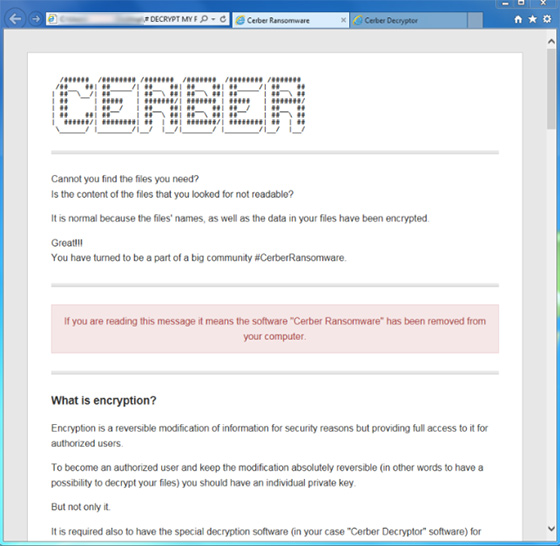
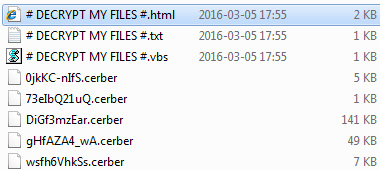
Filenames do not remain intact either. The ransomware substitutes them with strange-looking hexadecimal arrays, making a regular file look like 62eIcP12oQ.cerber. Obviously, this twisting prevents the user from even figuring out where exactly a random file of interest is. Having scrambled all the valuable data items on the hard disk, removable drives and networks shares, the infection throws in what’s called ransom notes into every folder. These are three files containing step-by-step directions on data restoration. Aside from the above-mentioned .vbs one, they include # DECRYPT MY FILES #.html and # DECRYPT MY FILES #.txt editions. The message is as follows, “Cannot you find the files you need? Is the content of the files that you looked for not readable? It is normal because the files’ names, as well as the data in your files have been encrypted. Great!!! You have turned to be a part of a big community #CerberRansomware.”
Obviously, the perpetrators are ironic to say so – they make it look like the attack is good news. In fact, it isn’t at all. Years of personal photos, videos, work documentation and tons of other files are under the risk of vanishing. The ransom notes recommend that the victim downloads and installs Tor Browser and opens their personal decryptor page. According to that page, the user is bound to purchase special software – “Cerber Decryptor” – for 1.24 Bitcoins, which is around $800. Unless the person sends the payment during 7 days, the size will double and become 2.48 Bitcoin. To let the user know how much time is left before the increase, the page displays a countdown timer.
The bad news is that .cerber files cannot be decrypted for free. Months after the launch of this extortion campaign, researchers are still struggling to create a decryptor, to no avail. Fortunately, there are techniques that can help revive some data. Keep reading this tutorial to learn what those are and how to take advantage of them.
Cerber ransomware removal
It’s usually quite easy to get rid of the offending program proper. Ransom Trojans are easy targets for antimalware suites once the data encryption part has been performed. This fact alone does not set aside the necessity of removing the infection, because it may cause further damage along with the likely escorting modules such as password stealers.
1. Download, install and run Cerber removal software. Click the Start New Scan button and wait until the suite does a thorough system checkup.
Download Cerber ransomware remover2. When the scan results are readily available, go to Fix Threats and let the program do its cleaning job.
Workarounds to recover .cerber files
Unless security researchers or AV labs release a dependable decrypt tool, recovering the scrambled files is somewhat of a lottery. However, there are techniques that ransomware victims shouldn’t fail to try before considering the buyout suggested by the criminals. Be sure to peruse and implement the methods below.
1. Backups
First and foremost, download backup copies of your important data from an offsite storage unaffected by the ransomware. In case you hadn’t had a backup strategy before the breach occurred,
proceed to the next step. Also, start maintaining secure backups of the most valuable information so that attacks like this one won’t cause that much damage in the future.
2. Shadow Copies
First and foremost, download backup copies of your important data from an offsite storage unaffected by the ransomware. In case you hadn’t had a backup strategy before the breach occurred,
proceed to the next step. Also, start maintaining secure backups of the most valuable information so that attacks like this one won’t cause that much damage in the future.
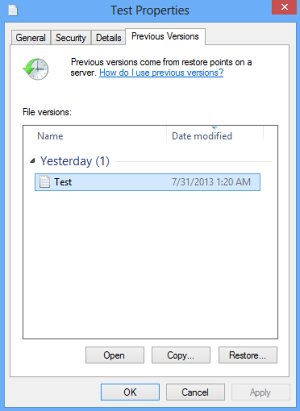
- Previous Versions Based on Restore Points
Select a random encrypted file, right-click on it and go to Properties. Now proceed to the Previous Versions tab. If the OS had been making snapshots of this file during system restore events, it will display the list of available file versions. Highlight the latest one and select Copy to recover it to a new path on the computer. Clicking the Restore button will reinstate the file to its original location.
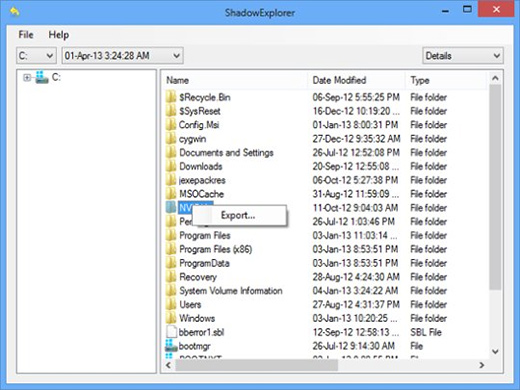
- ShadowExplorer
The applet called ShadowExplorer is meant to automate data recovery based on VSS (Volume Snapshot Service). If that’s the workflow of your choice, download and install the tool. Run it, select the local drive name and the folder of interest, right-click on it, hit the Export option and follow further prompts to get the job done.
3. Forensic Tools
The algorithm of data scrambling employed by most ransomware involves the deletion of original files, while their encrypted copies are the objects of the ransom bargain. Now, erasing
information off the hard drive is only irreversible when done with multiple overwrites. Otherwise, it may be possible to restore files using utilities like
Data Recovery Pro. Simply run the app and see whether it can do the trick.
Look before you leap into secure computing
Now that you have hopefully recovered your files, make sure the Cerber ransomware will make no more trouble. Consider scanning the system for executables and leftover registry keys added by the infection. Double-checking is also a good idea because some of the newer variants of crypto malware are accompanied by other threats such as rootkits and identity theft programs. So run the scan again and see whether or not you are completely safe.