Decrypt and remove Zepto ransomware: How to recover .zepto files
This guide presents a comprehensive overview of the file-encrypting virus called Zepto and provides file recovery methods that don’t involve ransom payment.
Perhaps the Zepto ransomware wouldn’t have called forth such a fuss in the IT community from the start if it weren’t for the fact that it’s a successor of another nasty malady called Locky. The predecessor stayed in the very top of all ransomware campaigns for more than three months, with thousands of drive-by downloads around the globe and millions paid in ransoms. The two have a striking external similarity, including the design and text of ransom note, as well as the Tor page used for accepting payments from victims. Furthermore, the main propagation vector is the same. Zepto also arrives at Windows PCs with phishing emails sent through the aid of a botnet dubbed ‘Necurs’. When a user encounters such a message in their mail inbox and opens it out of curiosity or by accident, the ZIP package automatically deploys the malicious code in the system.
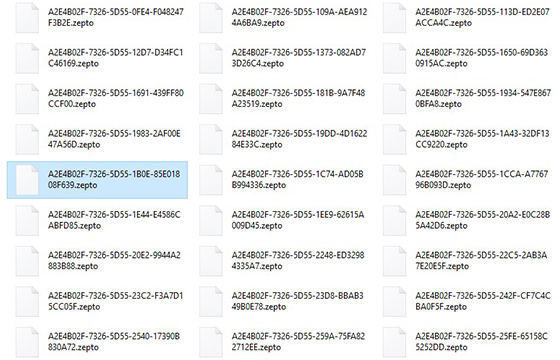
Another property in common is that Zepto hits removable drives, network shares and backup drives along with local volumes on the hard disk. The scope of data covered, therefore, may deprive the infected person of all their valuable information. The new features, however, allow for easy delineation of these samples. The currently active sample got its name from the .zepto extension that it appends to every single data file. The structure of affected filenames is different, too. The original ones are replaced with five blocks of hexadecimal characters; consequently figuring out which one corresponds to a particular file is a no go.
The cryptographic facet of Zepto is implemented professionally enough to make brute forcing futile, but it isn’t new. On the first stage, the ransomware encodes a random file with the AES standard using a 128-bit key. To protect this key from being retrieved by the victim, the offending app then encrypts it with RSA, where the entropy is much higher. The only 100% viable way to restore data relies on the availability of the private RSA key, but the problem is that this missing fragment is in the criminals’ hands.
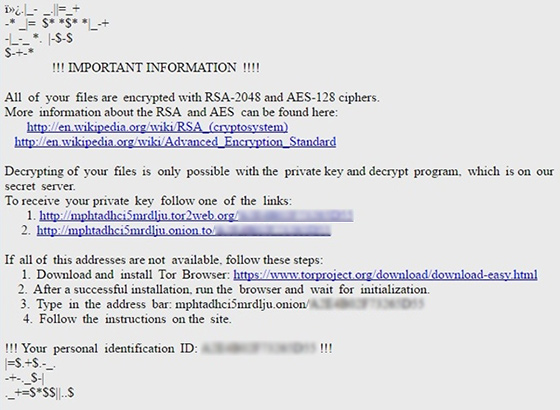
Zepto tells the victim what’s going on through a set of avenues named “_HELP_instructions.bmp” and “_HELP_instructions.html”. To make sure the user actually reads those, the virus makes the BMP version supersede the desktop wallpaper. In a nutshell, the perpetrators inform the person about the fact of personal data encryption and recommend a fix. It presupposes that the victim follows their personal hyperlink over Tor Browser and submits 0.5 Bitcoin via the Decryptor Page.
Some people who have paid the ransom to Zepto authors still cannot restore their files because nothing happens and the decryptor doesn’t become available to download. This just proves that a deal with extortionists is thin ice. Instead of going this path, use the instructions below to get around the whole crypto part and get files back in a different way.
Zepto ransomware removal
It’s usually quite easy to get rid of the offending program proper. Ransom Trojans are easy targets for antimalware suites once the data encryption part has been performed. This fact alone does not set aside the necessity of removing the infection, because it may cause further damage along with the likely escorting modules such as password stealers.
1. Download, install and run Zepto removal software. Click the Start New Scan button and wait until the suite does a thorough system checkup.
Download Zepto ransomware remover2. When the scan results are readily available, go to Fix Threats and let the program do its cleaning job.
Workarounds to recover .zepto files
Unless security researchers or AV labs release a dependable decrypt tool, recovering the scrambled files is somewhat of a lottery. However, there are techniques that ransomware victims shouldn’t fail to try before considering the buyout suggested by the criminals. Be sure to peruse and implement the methods below.
1. Backups
First and foremost, download backup copies of your important data from an offsite storage unaffected by the ransomware. In case you hadn’t had a backup strategy before the breach occurred,
proceed to the next step. Also, start maintaining secure backups of the most valuable information so that attacks like this one won’t cause that much damage in the future.
2. Shadow Copies
First and foremost, download backup copies of your important data from an offsite storage unaffected by the ransomware. In case you hadn’t had a backup strategy before the breach occurred,
proceed to the next step. Also, start maintaining secure backups of the most valuable information so that attacks like this one won’t cause that much damage in the future.
- Previous Versions Based on Restore Points
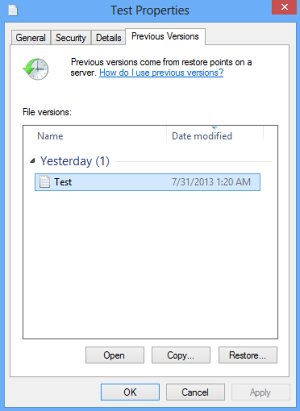
Select a random encrypted file, right-click on it and go to Properties. Now proceed to the Previous Versions tab. If the OS had been making snapshots of this file during system restore events, it will display the list of available file versions. Highlight the latest one and select Copy to recover it to a new path on the computer. Clicking the Restore button will reinstate the file to its original location.
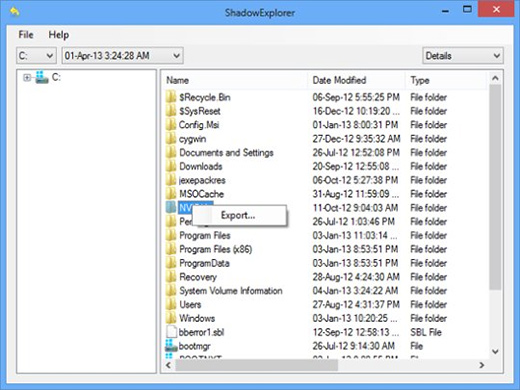
- ShadowExplorer
The applet called ShadowExplorer is meant to automate data recovery based on VSS (Volume Snapshot Service). If that’s the workflow of your choice, download and install the tool. Run it, select the local drive name and the folder of interest, right-click on it, hit the Export option and follow further prompts to get the job done.
3. Forensic Tools
The algorithm of data scrambling employed by most ransomware involves the deletion of original files, while their encrypted copies are the objects of the ransom bargain. Now, erasing
information off the hard drive is only irreversible when done with multiple overwrites. Otherwise, it may be possible to restore files using utilities like
Data Recovery Pro. Simply run the app and see whether it can do the trick.
Look before you leap into secure computing
Now that you have hopefully recovered your files, make sure the Zepto ransomware will make no more trouble. Consider scanning the system for executables and leftover registry keys added by the infection. Double-checking is also a good idea because some of the newer variants of crypto malware are accompanied by other threats such as rootkits and identity theft programs. So run the scan again and see whether or not you are completely safe.