Decrypt My Files virus: how to defeat Cerber2 ransomware
Version 2 of the Cerber crypto virus creates ransom instructions named Decrypt My Files inside folders with encrypted data, more details provided in this post.
Whereas some ransomware applications display scary alerts to victims, including horror movie-themed ones like in the Jigsaw plague incident, the newest variant of the infection called Cerber is a down-to-earth sample. Its ransom notes are concise and sufficiently informative at the same time, stating that all personal files have been ciphered and are therefore inaccessible, and providing first steps to start the paid decryption process. A combo of several different editions of these instruction objects is dropped into every single data directory with files whose extensions suddenly turned into .cerber2. In particular, having opened a random folder the infected user will see scrambled files and the following entries: # Decrypt My Files #.txt, # Decrypt My Files #.html, and # Decrypt My Files #.vbs. The image below demonstrates this predicament.
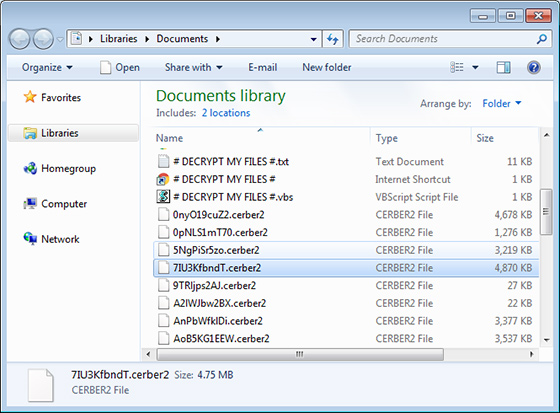
There is hardly any fundamental difference in the contents of the TXT and HTML versions. What both of these tell the victim is, “Your documents, photos, databases and other important files have been encrypted!” This text is followed by a few temporary links that the victim is supposed to follow to go to their personal page. The VBS edition of Decrypt My Files entry, however, is quite special. It is a piece of VBScript that activates the computer’s speakers and literally pronounces the warning message. This is a distinctive trait of Cerber and Cerber2 variants of the virus.
Before these events begin to occur, obviously, the compromise proper has to take place. This ransomware harnesses a complex network of PC infiltration vectors, including exploits kits and banal spam. In the former scenario, there isn’t much that the user can do to prevent the attack other than stay away from hacked websites. This may be problematic because there are usually no explicit indicators of a hack. From the page, the person is redirected to a malicious landing page with the exploit kit on it, and software vulnerabilities on the computer are used to inject the ransomware. The spam-based infection avenue is simpler and easier to thwart, where the main preemptive measure is not to open suspicious email attachments masqueraded as official documents.
The Decrypt My Files ransomware virus reroutes its victims to the Cerber Decryptor site, where the amount of the ransom is indicated. It’s typically on the order of 1.5 Bitcoins, and it increases two times if the initial sum is not submitted to the criminals within 5 days. A real-time deadline countdown is embedded into the page as well. In order to be on the safe side, the best recommendation is to keep data backups in a secure storage outside the computer. If there are no backups, decryption after the fact is impossible because Cerber users an unbreakable AES-256 algorithm. A number of alternative methods to overcome the problem are provided below.
Decrypt My Files ransomware removal
It’s usually quite easy to get rid of the offending program proper. Ransom Trojans are easy targets for antimalware suites once the data encryption part has been performed. This fact alone does not set aside the necessity of removing the infection, because it may cause further damage along with the likely escorting modules such as password stealers.
1. Download, install and run Cerber removal software. Click the Start New Scan button and wait until the suite does a thorough system checkup.
Download Decrypt My Files virus remover2. When the scan results are readily available, go to Fix Threats and let the program do its cleaning job.
Workarounds to recover encrypted files
Unless security researchers or AV labs release a dependable decrypt tool, recovering the scrambled files is somewhat of a lottery. However, there are techniques that ransomware victims shouldn’t fail to try before considering the buyout suggested by the criminals. Be sure to peruse and implement the methods below.
1. Backups
First and foremost, download backup copies of your important data from an offsite storage unaffected by the ransomware. In case you hadn’t had a backup strategy before the breach occurred,
proceed to the next step. Also, start maintaining secure backups of the most valuable information so that attacks like this one won’t cause that much damage in the future.
2. Shadow Copies
The ‘Decrypt My Files’ virus is coded to obliterate Shadow Copies of its victim’s files, which are data snapshots automatically made by the operating system. The ransomware has reportedly
failed to complete this task in some cases, though. An important prerequisite of successful recovery is the ‘enabled’ status of the System Restore feature prior to the compromise.
There are two ways to take advantage of this functionality built into Windows.
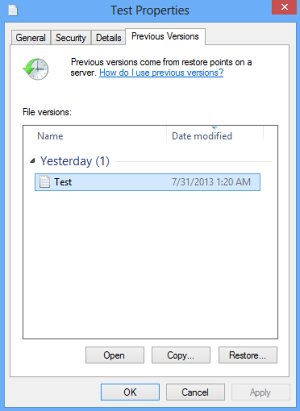
- Previous Versions Based on Restore Points
Select a random encrypted file, right-click on it and go to Properties. Now proceed to the Previous Versions tab. If the OS had been making snapshots of this file during system restore events, it will display the list of available file versions. Highlight the latest one and select Copy to recover it to a new path on the computer. Clicking the Restore button will reinstate the file to its original location.
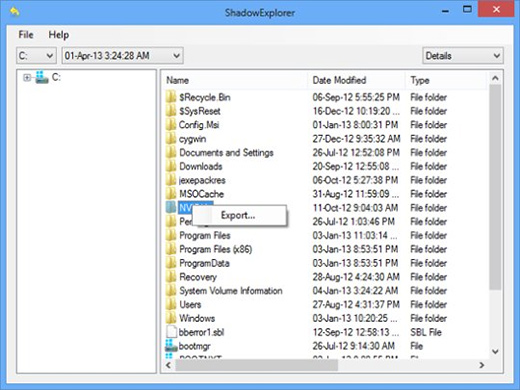
- ShadowExplorer
The applet called ShadowExplorer is meant to automate data recovery based on VSS (Volume Snapshot Service). If that’s the workflow of your choice, download and install the tool. Run it, select the local drive name and the folder of interest, right-click on it, hit the Export option and follow further prompts to get the job done.
3. Forensic Tools
The algorithm of data scrambling employed by most ransomware involves the deletion of original files, while their encrypted copies are the objects of the ransom bargain. Now, erasing
information off the hard drive is only irreversible when done with multiple overwrites. Otherwise, it may be possible to restore files using utilities like
Data Recovery Pro. Simply run the app and see whether it can do the trick.
Look before you leap into secure computing
Now that you have hopefully recovered your files, make sure the Cerber ransomware will make no more trouble. Consider scanning the system for executables and leftover registry keys added by the infection. Double-checking is also a good idea because some of the newer variants of crypto malware are accompanied by other threats such as rootkits and identity theft programs. So run the scan again and see whether or not you are completely safe.